Hooshyarane Vatan hack Safiran

The cyber group known as Hooshyarane Vatan has once again exposed an Iranian company working with the IRGC. Read about their previous attack here and here. This time it is Safiran airport services who have been facilitating weapons and UAV deliveries to Russia.
On 17 June, the group released more than 1 gig of data from a Safiran email server on its Telegram channel (here) that they claim to have easily accessed due to poor security. The group also announced they had deleted all data from this email server.
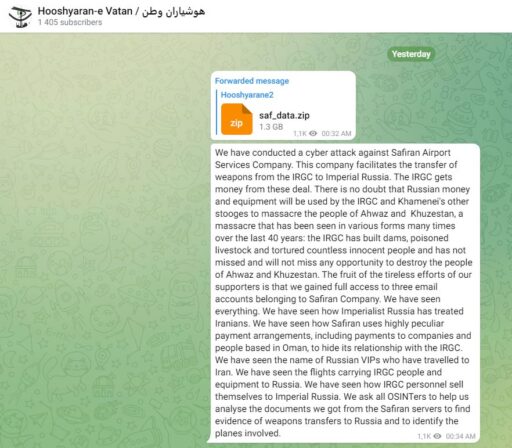
What is in the data?
Amongst the large amounts of data published so far is proof that Safiran is using a front company called Dark Blue which is based in Dubai and using a bank in Oman to receive payments for services.
An interesting point is the sections highlighted in the picture below which proves Safiran are knowingly evading sanctions – They ask there is no reference made of Safiran in the payment details.
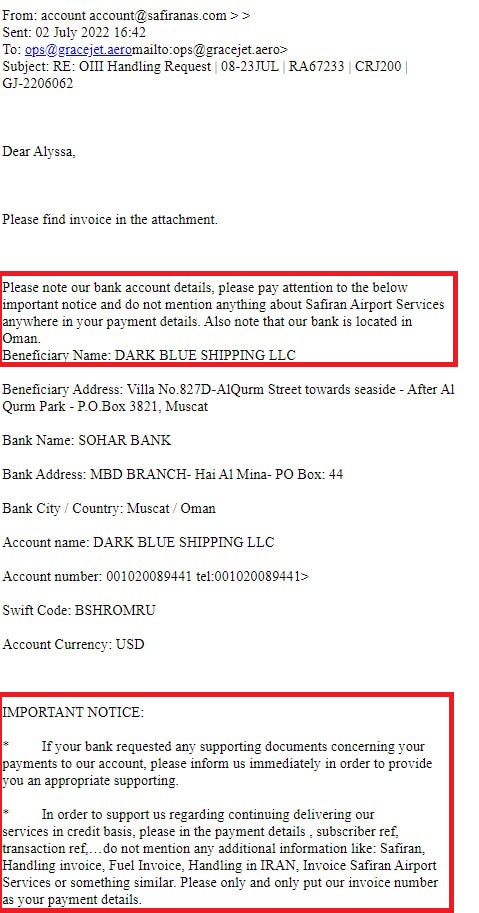
Hooshyarane Vatan revealed the front company as:
Office 1401B, Floor 14, Latifa Tower (East Wing), Sheikh Zayed Road, Dubai, UAE.
Darkblueshipping.com
Darkbluetradingllc.com
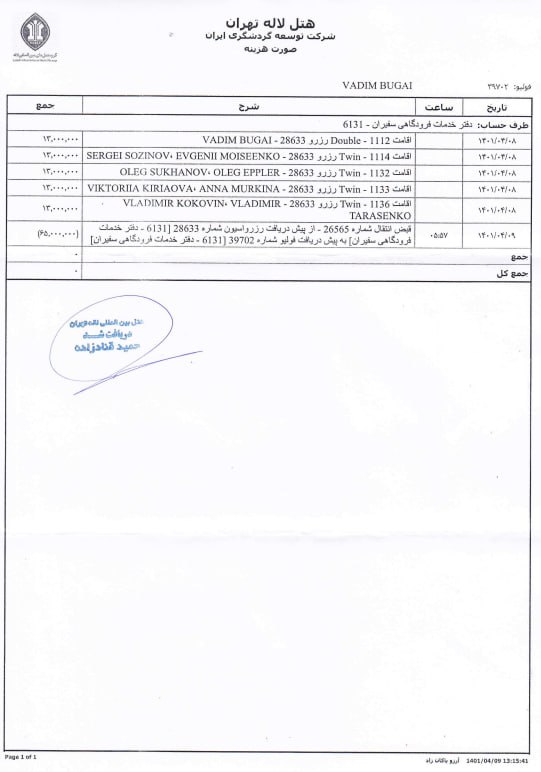
Russian visitors
The data also shows that many Russians have traveled to Iran and have stayed in luxury hotels. A contrast to the conditions of their compatriots in Ukraine.




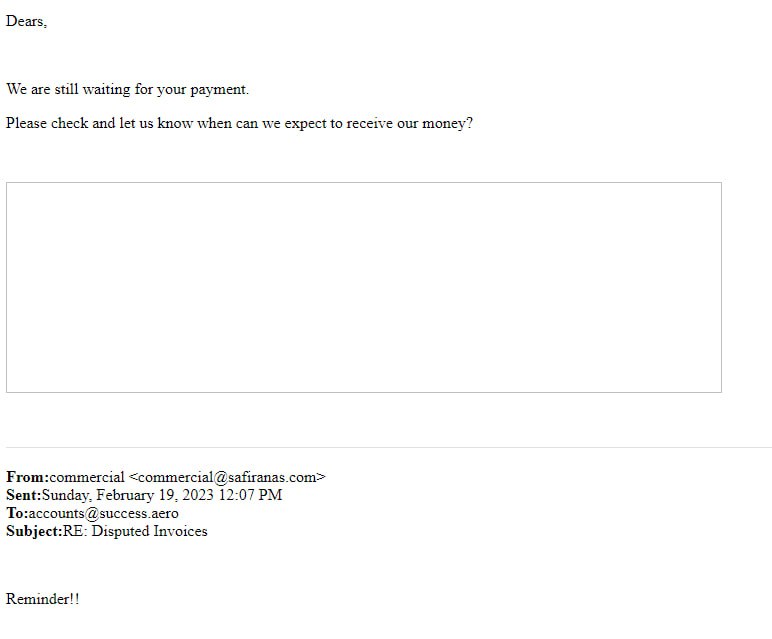
The data also shows that Russia refuses to pay for Safiran’s services who have repeatedly requested their money.
There is a lot of data which we are currently checking. We are planning to write a follow up with anything else we find. If you want to examine the data yourself let us know what you find by messaging us on Twitter (@IranCyberNews) or send an email to [email protected].
You can find the data file called saf_data.zip on Telegram – t.me/hooshyarane or see Twitter (@Hooshyaran1) for details of new leaks.
