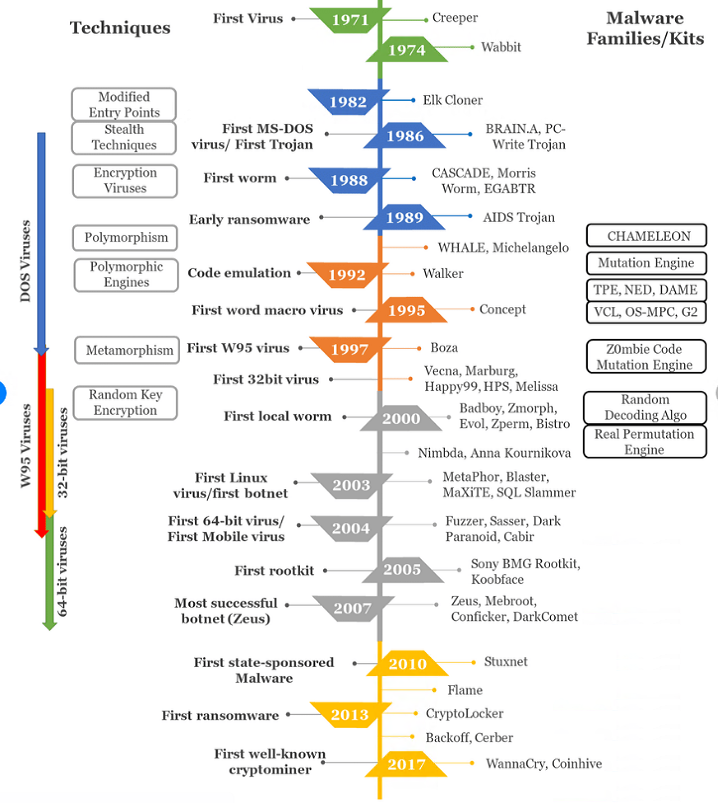
Famous Malware: Part four of the Hacker Series

Dear readers for part four of our hacker series will talk about some of world’s most famous malware. The tools are used by APTs to attack their victim and cause major damage
Emotet 2018
Mydoom 2004
The worst computer virus outbreak in history, Mydoom caused estimated $38 billion damage in 2004 but adjust for inflation cost is actually $52.2 billion. Also known as Novarg this malware is technically worm spread by mass emailing. At one point Mydoom was responsible for 25% of all emails sent
The malware scrapped addresses from infected machines then sent copies of itself to those address, it also built botnet with infected machines and performed distributed denial of service attack (DD0S) on victim servers. Still active today Mydoom generates 1% of all phishing email sending 1.2 billion copies of their own per year. a $250,000 reward was offered for the developer Mydoom but they have not been caught
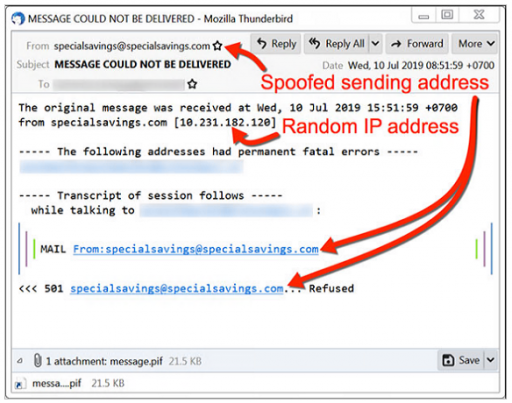
EternalBlue 2017
Created by the NSA this exploit became public in April 2017 when a group of mysterious hackers known as the shadow brokers published the code online. After its release it was first used in cryptocurrency mining campaigns but it became well known when it was used as part of three ransomware attacks in 2017 known as WannaCry NetPetya and Bad Rabbit.
EternalBlue is still used by cyber criminal and APTs as a mechanism for spreading to other systems inside compromised networks by exploiting wrongly configured SMBv1 clients on Windows computers
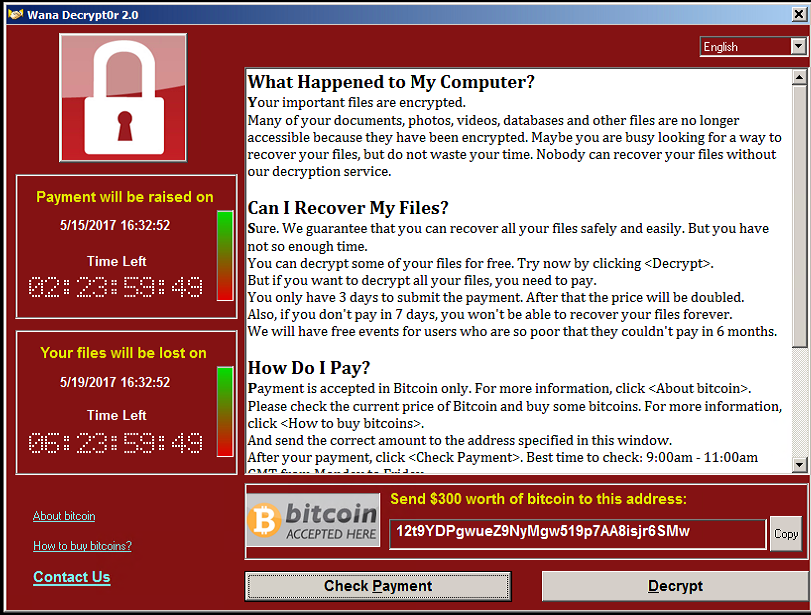
WannaCry 2017
WannaCry was developed in 2017 by North Korean state hacker in order to infect victim system and collect ransom for the Pyongyang regime which is under heavy economic sanctions. The malware infected an estimated 3 million computers and was particular controversial for its propagation. Once infected WannaCry encrypts files on the computer hard drive, denying access to any data on the system. In return, the victim is forced to pay a ransom via bitcoin to decrypt their data. In a major attack a new variant forced TAiwan Semicondutor MAnufacturing Company (TSMC) to temporarily shut down its manufacturing facilitates to control the spread in 2018
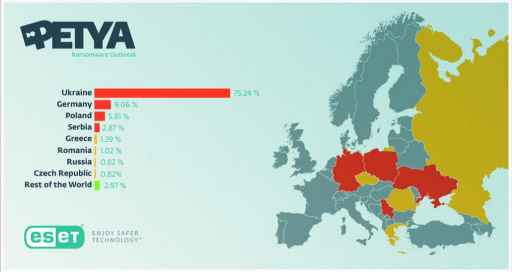
NotPetya 2016
Soon after WannaCry attack a second ransomware outbreak hit the world. Although first discovered in 2016 this malware called NotPetya made by Russian APT Fancy Bear was initially used to attack Ukraine in 2017. Due to shared networks and enterprise VPN’s the ransomware spread globally causing billions in damage. Just like WannaCry it used EternalBlue as its worm component allowing it to infect large numbers of system
Stuxnet 2010
Stuxnet was a sophisticated malware attack against Iran’s Natanz nuclear power facilities. The worm was reported as being developed by Israeli and US intelligence agencies although no one has openly taken responsibility
Stuxnet was originally designed to target programmable logic controllers used to automate the elector mechanic and machine process within the facilities centrifuges. It was also one of the first known cases of a computer program capable of breaking hardware.
Although the malware was designed to expire in June 2021 since then other malware based on its code and characteristics has continued to wreak havoc on industries around the world
Storm Worm 2007
During large storms in Europe thousands of users received malicious email disguised as weather information. The email had attachment that when opened infected victims with a Trojan horse malware. The malware spread to 1 million computers in Europe and America
The malware had the characteristics of a Trojan horse and a worm combining multiple layers of attacks, once infected, it would download a package of executable files on the affected systems. These files were used to carry out various functions including stealing sensitive user information, delivering spam emails to spread more malware and launching Distributed-Denali-of-Service (DDoS) attacks.
Uroburos 2008
Our final famous malware Uroburos was the rootkit developed by the infamous Turla group, one of the worlds most advanced nation-state hacker groups, linked to the Russian government. According to a report from Germany cyber experts G DATA the rootkit was able to take control of infected machine execute arbitrary commands and hide system activities. Uroburos also referred to as the Turla or Snake rootkit was widely deployed and was very efficient for the limited purpose it was being used for – to gain boot persistence and download other malware
It was the central piece of Turla APT attacks and had been seen on infected computers in the Middle East, Europe and the US as early as 2008. Targets usually included government entities, it was seen in 45 countries and a further Linux variant was discovered in 2014
Summary
My friends there are many famous malware since first Creeper virus infected machines in 1971 . Computer virus cost $55 billion each year to repair. the biggest computer virus ever is the Mydoom virus which cost $38 billion in damage. Other notable attack are Sobig worm which cost $30 billion and Klev worm that did $19.8 billion in damage. Every day hackers design new ways to infect victim machines but thankfully today secure PC and operating system make it very hard for virus and worm to get into our system
The best way to beat the hackers is to insure your systems have up to date antivirus and people are aware of the risks when they are online
To see earlier article on our Hacker Series click below
Advanced Persistent Threats: Part one of ICNAs Hacker Series
Charming Kitten; Part two of The Hacking Series
Fancy Bear; Part three of The Hacking Series
