Advanced Persistent Threats: Part one of ICNAs Hacker Series
ADVANCED PERSISTENT THREATS

Dear readers in our previous article titled The increasing problem of hacking in Iran we talked about different hacking groups operating in our country. In the coming weeks we will publish a number of articles as part of a new series of hackers that will talk about the ongoing advanced persistent threats posed around the world. There are hundreds of groups but we focus on the most active groups that we will take a special interest in Iranian groups.
What is an Advanced Persistent Threat
Before we start talking about specific groups we need to take the time to talk about what is meant by advanced persistent threats or APT as they are known. According to Kaspersky Lab APTs is a group of hackers who use continuous, covert and sophisticated hacking techniques to gain access to systems and stay inside for long periods of time with potentially destructive consequences.
What makes them different to other cyber criminals
The term APT was first used in the early 2000s but these groups have probably been active since the early days of the Internet. according to cybersecurity experts the difference between an APT group and other hacking groups can be divided into four parts
- Attacks by APT groups are more sophisticated and complicated than usual hacks
- APT groups consist of highly qualified, capable and elusive members with deep technical background
- The motivation behind the hacking group are often financial or political while the motivations behind APT groups are most of the time strategic
- In general APT groups are nation state or state-sponsored who have much better advanced devices and are already financially covered
Because of the level of effort required to carry out such attacks APTs are usually target high-value targets such as national governments and corporations. The usual goal is to steal information over a long period of time rather than simply enter and exit them quickly. Black hat hackers carry out cyber attacks on the lower level
Although APT level attacks should be on the radar of any major business it does not mean small and medium sized companies can ignore this type of attack. APT attackers are increasingly using smaller less secure businesses that make up the supply-chain of their ultimate target as way of gaining access to large organizations
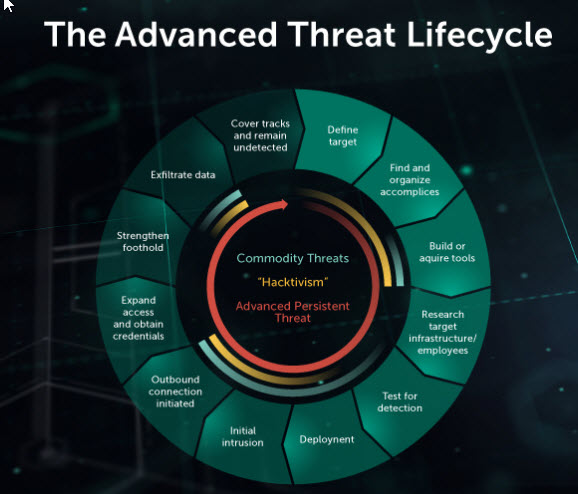
The five stages of an evolving advanced persistent attack
The whole purpose of an APT attack is to gain ongoing access to its victim system, a hacker achieves this in five steps
Stage one: Gain Access
Like a thief forced to open the door cyber criminals gain entry the victim system using of infected files, application vulnerabilities and unaware employees clicking on malicious links
Stage two: Creating a foothold
In the next step the attacker has planted malware that allows the creation of a network of backdoors and tunnels that can be used to navigate systems without detection
Stage three: Deepen access
Once established inside the victims network hackers use techniques such as password cracking and privilege escalation to gain administrator rights allowing them to gain control of more system and gain even greater levels of access
Stage four: Lateral movement
Deeper inside the system using the admin rights they gains in the third stage the attacker can move around the victim system as he pleases, they can also attempt to access over servers and secure parts of the network
Stage five: Look learn and stay
From within the system criminals will have a thorough understanding of how the network works and its vulnerabilities. they will use this information to collect all the data they want
They try to continue this process until they are detected or until they achieve their goals. They will often leave a back door to access a compromised system in the future
Conclusion
In the coming weeks we plan to write about some of the more popular APTs from countries such as China, Russia, USA, North Korea and here in Iran.
Look forward to our first article in this new Hacker Series when we tell you about one of our APTs Charming Kitten also known as APT35