Pegasus Spyware and the commercialization of spying

Guest written by: Laurrits Vestergaard
Spying on personal communications is not new, it has been undertaken by governments for decades. However, the discovery of the extent of use of the Pegasus spyware in 2016 and subsequent research by Citizen Lab, the Pegasus Project and Amnesty International have revealed a scale and diversity of targets, alongside a level of access into private communications, which is unprecedented. Spyware is a piece of software with malicious behavior which is designed to gather information about a person or organization and send it to another entity in a way that harms the user; these behaviors can be exhibited by web or advertising tracking but key to spyware is the lack of knowledge of the user. Pegasus spyware can be brought from a private company – spyware is no longer the domain of only governments with resources, wealth and skills to be able to develop this type of spyware internally.
Pegasus is a piece of malicious software which can by installed on a mobile device, either iOS or Android, which was developed by the Israeli cyber-security company NSO Group who markets and licenses Pegasus to governments around the world. Since being first identified in 2016 this software has become increasingly sophisticated and is now utilizing zero-click exploits and does not require any user action to successfully be installed onto a device. This means that the owner of the device will have no knowledge that Pegasus spyware is present on their devices. Once installed, Pegasus has access to virtually any data on the device – including SMS, messages, address books, browsing history, GPS data, photo galleries and call history. It can even be used to turn on the microphone and camera to turn the device into a covert listening device. All of this data can be exfiltrated from the device. This gives the people behind the spyware install access to some of the most personal, private communications and content in many people’s lives.
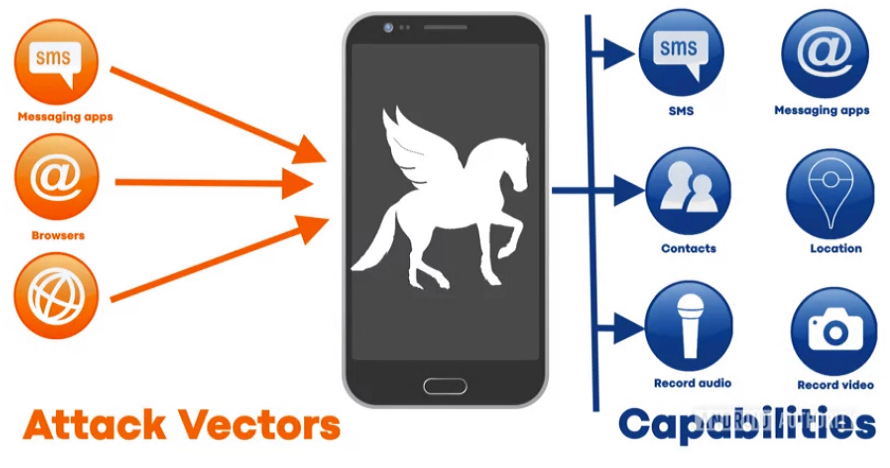
NSO state that the spyware is only meant to target serious criminals and terrorists. While the definition of terrorist and criminal activities varies between states; there is no doubt that these two realms are not the sold prerogative of Pegasus Spyware. The findings of the groups including Amnesty International, the Pegasus Project and Citizen Lab reveal from a forensic examination of a leaked list of over 50,000 phone numbers which were used by customers of NSO for surveillance and the forensic examination of targeted devices tell a different story. This indicates that individuals who were targeted by Pegasus spyware were not solely criminal or terrorism-connected individuals. This spyware has been used to target heads of state, activists and journalists among others. Research by Amnesty international has identified the use of Pegasus spyware against human rights activists and journalists worldwide. These is a growing body of evidence that this is directed by governments specifically targeting activists and others speak out against abuses of power. Journalists and rights defenders have been targeted across the world including recently in Jordan; with research by Citizen Lab connecting this activity to potential agencies of the Jordanian government.

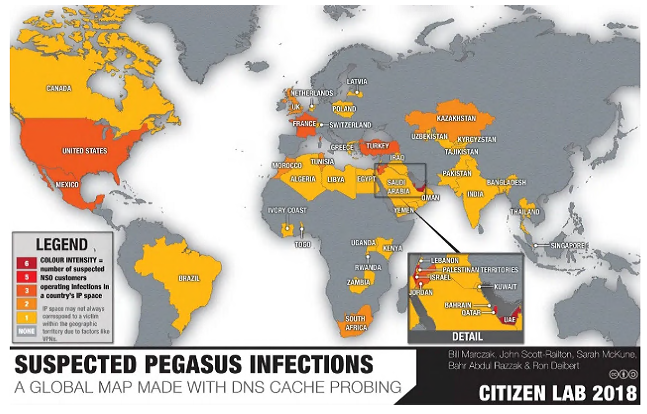
Additionally, one individual targeted by Pegasus spyware is Lama Fakih, Crisis and Conflict director and Head of the Beirut Office at Human Rights Watch. She oversees crisis response for a range of countries and as part of this role she documents and exposes human rights abuses. She is not an individual who would be classed under any definition as a ‘terrorist’ or criminal and yet her phone was still attacked and had Pegasus installed covertly. This is not an outlier or one-off, there is a large and expanding list of activists, journalists, politicians, diplomats across countries including Palestine, Poland, Uganda and Bahrain who have had Pegasus Spyware implanted on their devices. This repeated, systematic and broad targeting of these individuals destroys NSO claiming that their spyware is solely licensed to governments or law enforcement to fight terrorism and crime; rather implies it is licensed to those who can afford it and who they target is disregarded. The targeting of these individuals indicates systematic breaches of human rights and potentially an intention to discredit activists and organizations preventing and bring to light injustices, abuses and breaches of international law across the world.
While Pegasus spyware is the most famous, it is not the only example of commercial spyware available. The industry is growing with an increasing proliferation of companies providing this technology and in 2022 could potentially be worth about twelve billion dollars. Although these sorts of estimates are always uncertain; it is clear that commercial spyware is a huge and growing industry-with an increasing number of governments willing to buy and use these products. However, this industry remains obscure and lightly regulated; often there is minimal due diligence from companies regarding the human right violations resulting from the use of their spyware. This is not a hypothetical situation-the numerous cases where journalists and activists have discovered this software installed on their devices is likely to violate their right to privacy and there are indications that some governments use of this spyware could have led to torture and enforced disappearances.
There needs international regulation of this technology much in the way that other arms control measures have been created and agreed between nations. Without this regulation these will be no change in the current situation,
For those who have already been subjected to this spyware there is no recourse as they are faced with just lines of malicious, silent code.
