Malware: Iranian ISP spearphished to spread awareness of IRGC malicious activity

Iranian ISPs spearphished to reveal IRGC use of malware
a large spearphishing campaign has targeted at least two Iranian ISPs according to ICNAs contacts within Shatel and Respina. The intent of the spearphishing does not appear to be malicious in nature but does blame the IRGC intelligence unit for conducting malicious activities with the use of malware.
The email claims that IRGC are responsible for developing this ransomware to exploit and profit from the victims of their attacks while Iranian people suffer. The full content of the email was provided to ICNA and can be found below:
Subject:
for your information
Body:
The IRGC Intelligence Unit is ransoming data for profit while the people suffer. This will only bring more sanctions and economic pain. Why does the IRGC support such activity? They are greedy and selfish and do not have the Iranian people’s interests at heart.
IRGC accused of developing and distributing malware
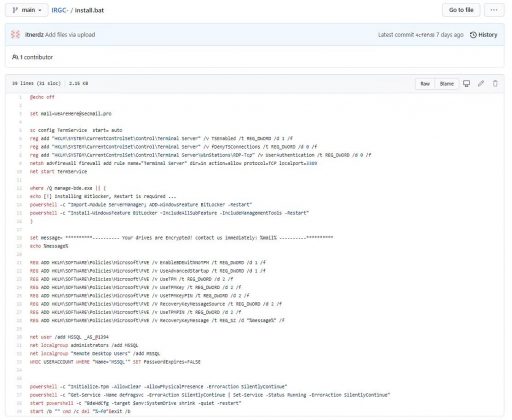
A copy of the malicious file was provided to us that reveals the malware configures a system for remote access and enables BitLocker and this does not seem like a very sophisticated or complex piece of code. Contact information is provided and is probably to be used for negotiation of ransom payment.
The email leads you to believe that the file is from IRGCs ransomware activity. This being so we made a search of VirusTotal (and VirusKav) and revealed that the malware file is also uploaded to these platform and that means the malware set will basically be useless as all the large antivirus software companies will already have a copy and will be scanning against this malware.
Iranian hacking landscape takes another defeat
Iran hackers have been often in the news it seems, and we have recently written about the identification of previous Iranian hackers such as Reveng3rs, N3tworm, Black Shadow and now we have example of what seems like an unsuccessful attempt by the IRGC at some ransomware activity to raise money.
With the USAs political attentions focused on stopping malicious cyber activity as seen at the G7 as well as the general stance it takes with countries like Russia it would seem counterproductive for IRGC to engage in reckless and unsophisticated cyber attacks at such a pivotal time such as negotiating the JCPOA and risk sanctions against Iran being lifted.

