Iranian malware attacks CORRUPT KITTEN, DOMESTIC KITTEN and ZOOPARK – what we have learnt
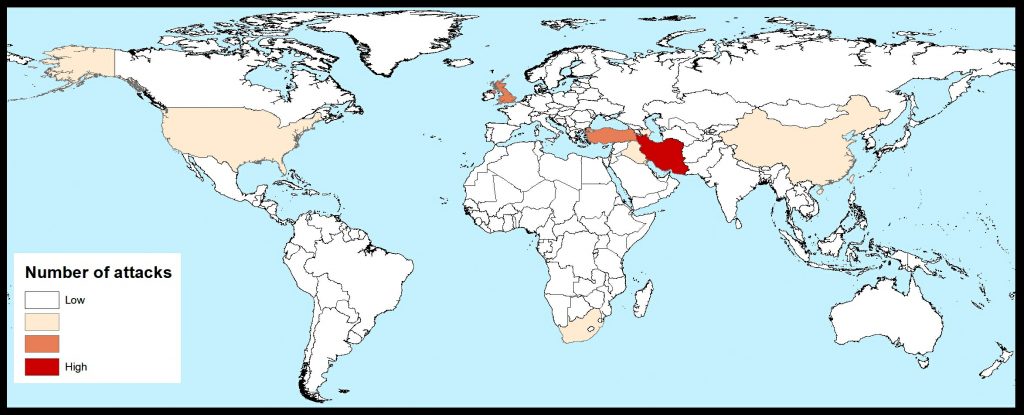
We have already published an article detailing the shocking intrusion of the Iranian government into the lives of the citizens they have sworn to protect. It was found that they actively use malware to violate the privacy of innocent Iranians and obtain very personal details which could be used against them.
Named CORRUPT KITTEN, the malware’s capabilities make a mockery of the government’s claim to stand for the protection of Iranians, instead betraying the trust that we have put into them. If the malware was installed on your device you could expect to have your contacts, files and photos, browser history and SMS messages viewed. Other messaging apps would not be safe to use either. With attackers able to upload a file from the device to their servers, even services that encrypt messages in transit like WhatsApp will not protect your data, as these messages are not encrypted when they’re saved on the device. In addition, access to your apps means that your location is not safe, your recorded audio can be listened to, and your camera can be used to spy on you.
Most disturbing of all, the malware allows the attacker to take control of your device. This means that as well as viewing every webpage you’ve been to and seeing private messages meant only for loved ones, the attacker can delete important information, attach your photos to a message of their own creation and send them to anyone in your contact list or even plant incriminating evidence. The gives attackers opportunity and power, as they could quite easily use the malware for blackmail or retribution, potentially using it to destroy reputations, careers and relationships. Nobody should have that kind of control over its people.
With such an intrusive level of access, it was hoped that the malware had only been seen in a few isolated incidents. Unfortunately, this is not the case. The source who found the malware, who wants to remain anonymous, stated that it is far more widespread than feared, targeting primarily Iranian citizens. With its level of sophistication, the ICNA determined that it could only have been created by the military or government.
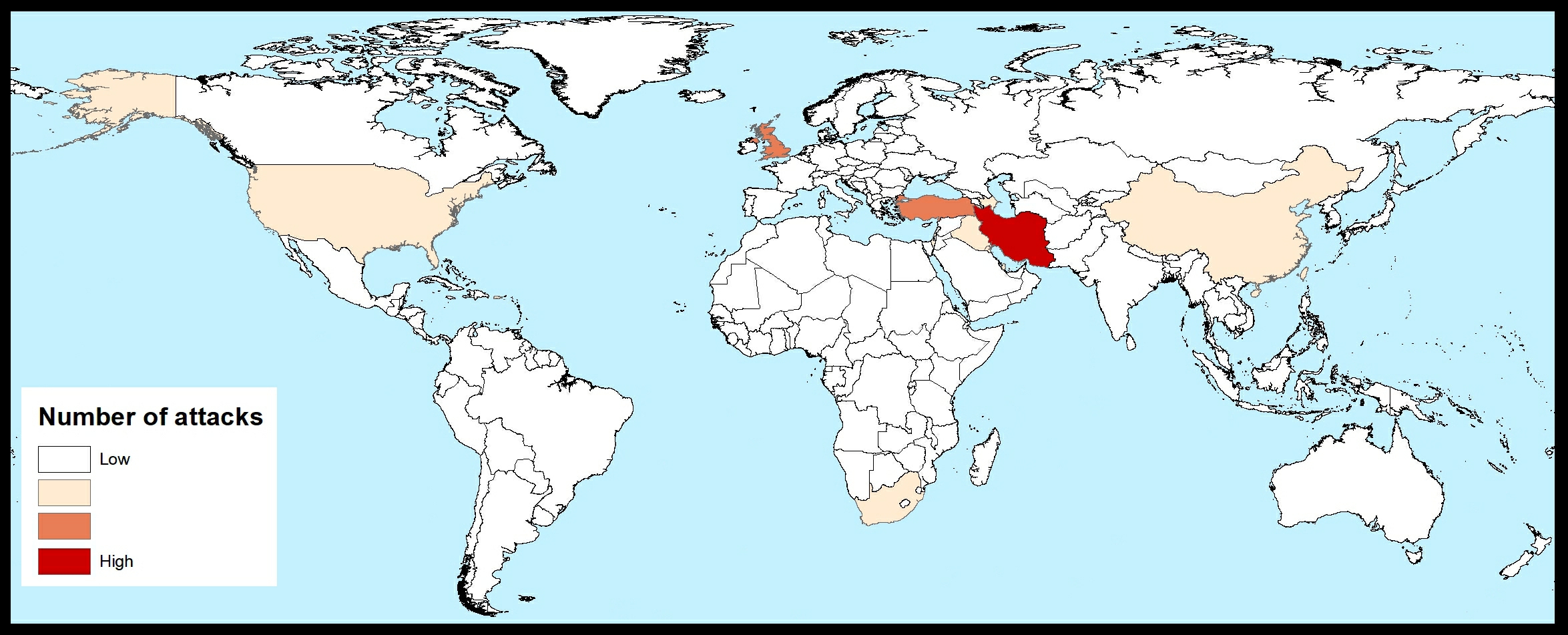
This malware itself was a beaconing implant which can be tasked by a beacon module using Hyper Text Transfer Protocol (HTTP) based communications. The C2 server was found to host an apparently fake website called “PINE STATE FLOWERS” with the domain name not relating to the content of the site. There have been at least five versions of this malware (see table for more details).
This is actually only the latest attack in a series of incidents that combined demonstrate the government’s increasing desire to meddle with the lives of its people. Previously, Iranian surveillance operations by the name of DOMESTIC KITTEN and ZOOPARK used similar capabilities that indicate a long-term campaign intended to take away Iranians privacy. In 2016, DOMESTIC KITTEN used fake decoy content that caused victims to download mobile applications that were believed to be of interest to them. These applications were loaded with spyware to collect sensitive information. As with CORRUPT KITTEN, DOMESTIC KITTEN allowed attackers to collect data like contact lists, phone call records, SMS messages, browser history and geolocation. Similarly, it was determined to be a government led operation and 97% of the victims were Iranian citizens.
ZOOPARK is sophisticated campaign that has been running for multiple years. This time, victims in Middle Eastern countries were spied on with malware via news websites that had been hacked by attackers, with themes including ‘Kurdistan referendum’, ‘TelegramGroups’ and ‘Alnaharegyptnews’. Visitors were then redirected to a downloading site that serves malicious APKs. After being downloaded data could be exfiltrated from the default applications on the device and also messaging applications like Telegram and WhatsApp. ZOOPARK was also considered to be a state-backed campaign, and was potentially developed by MOIS.
- Malware is a beaconing taskable implant using HTTP based communications
- Commands are requested by a beacon module placed in the commands table
- Tasks are runnable java objects and exist in their own thread. Upon completion the task object writes its results to disk with an entry in the data table
- An exfiltration module reads the data table and uploads results to infrastructure.
- SMS/MMS messages
- Phone records
- Contacts
- Browser history
- External storage
- Application list
- Clipboard content
- Geo-location and camera photos
- Surrounding voice recordings
- Device and software info
- Live screen recording
- Delete a file
- Turn Wi-Fi/Bluetooth on/off
- Take a picture
- Record sound and video
- Iranian nationals were the primary targets of this campaign
- The Iranian government or military due to sophistication of malware.
- Malware was operated from inside Iran
- Fake apps were designed for target groups such as ISIS supporters
- Theses apps contained malware which when downloaded would collect information on the victim
- The data was then exfiltrated to C&C servers using HTTP POST requests
- SMS/MMS messages
- Phone records
- Contacts
- Browser history
- External storage
- Application list
- Clipboard content
- Geolocation and camera photos
- Voice recordings
- 97% of the targets were Iranians
- Likely the Iranian government due to attack infrastructure and similarity with previous government-sponsored Iranian attacks
- Malware redirects visitors from news sites to a downloading site that serves malicious APKs
- Is distributed primarily through Telegram channels and ‘watering holes’
- Data is exfiltrated from applications on the device, targeting Telegram, WhatsApp and Chrome web browser
Information harvested:
- SMS messages
- Phone records
- Contacts
- Browser history
- Application details
- Camera photos/videos/audio
- Application data from Telegram, WhatsApp, Chrome etc.
- Internal databases including passwords
Other capabilities
- Shell commands execution
- Silently sending SMS messages
- Making calls
Victims
- Users in Middle Eastern countries, primarily Iran, Egypt, Jordan, Morocco and Lebanon
Perpetrator
- state-backed campaign possibly MOIS
