Charming Kitten – Part two of The Hacking Series

Dear readers in Charming Kitten – Part two of our hack series will be talking about the Iranian hacking group more known as Charming Kitten. The group known as APT35 was first identified by cybersecurity firm FireEye in 2014 and designated as an APT-based nation state in 2017. This hacking group has been given a variety of names from the cybersecurity community, Microsoft calls them Phosphorus while FireEye calls them Ajax Kaspersky Security they call NewsBeef but for this article we will call them what they are most known as charming kittens.
Since their discovery 7 years ago the group has regularly conducted phishing campaigns targeting high risk user, hijacked accounts, deploying malware, and used alternative techniques to conduct espionage aligned with Iranian government interests
HISTORY OF CHARMING KITTEN ATTACKS
2014 – Thamar Reservoir campaign
The 2014 cyber attack had the aim of seizing victims email accounts and compromise their machines, when under control of Charming Kitten further attacks were launched against other targets. The group used a variety of techniques to achieve their goals including
- Breaching trusted websites to set up fake pages
- Multi-stage malware
- Multi spear phishing emails based on reconnaissance and information gathering
- Phone calls to target
- Messages on social networks
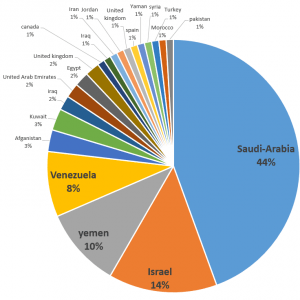
The majority of the campaigns victims were in the Middle East and belong to defense, journalist and human rights organizations
Although the success of these initial attacks was not technically complex and a number of errors were made, grammatical errors, an easy-to-reach attack infrastructure to bypass anti-analysis techniques and a lack of code obfuscation meant that the security community was easily able to identify the motives and origins of the groups
2016 – Magic Hound campaign
In 2016, Charming Kitten ran a campaign targeting state-owned, technology and energy companies with ties to Saudi Arabia. The group was seen to improve its tactics and techniques during the campaign using different tools with each new attack, this was an improvement over their previous attack in 2014.
One technique used by the group was to place Microsoft word and excel documents containing malicious macros on compromised legitimate websites or sites that resembled legitimate sites and when executed a spear phishing attack containing links to these files was carried out. If a victim clicks on these links malware will infect their systems allowing APT35 access to their networks.
2017 – HBO breach
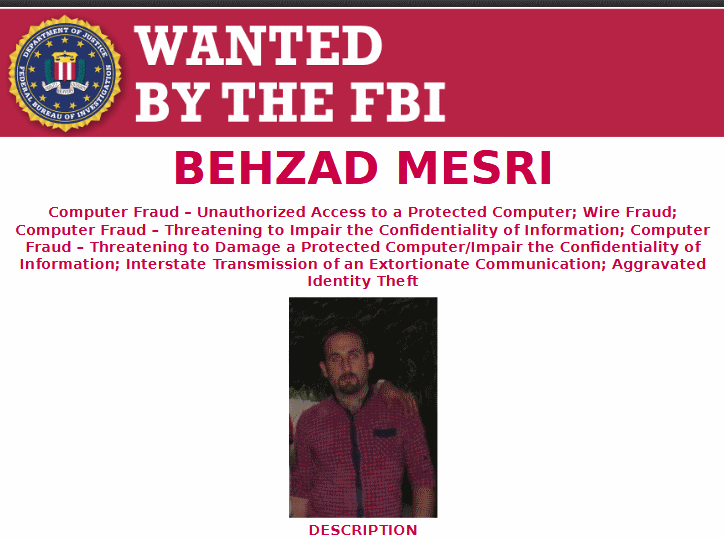
In 2017 Charming Kitten hacked into entertainment company HBO using Mr Smith online alias. Through the use of social engineering, phishing and malware they were able to access the HBOs network and steal 1.5 terabytes of data including films, scripts and other content, seven times as much data as sonys famous 2014 North Korean hack which we will cover in part five of our hacking series. The demand was $6 million BTC as ransom and the attackers released episodes of some top USA TV shows including a screenplay for an upcoming episode of game of thrones. Behzad Mesri who went by the pseudonym Skote Vahshat was charged by the Americans however he remains out of reach of US officials in Iran.
2020 – Fake interview campaign
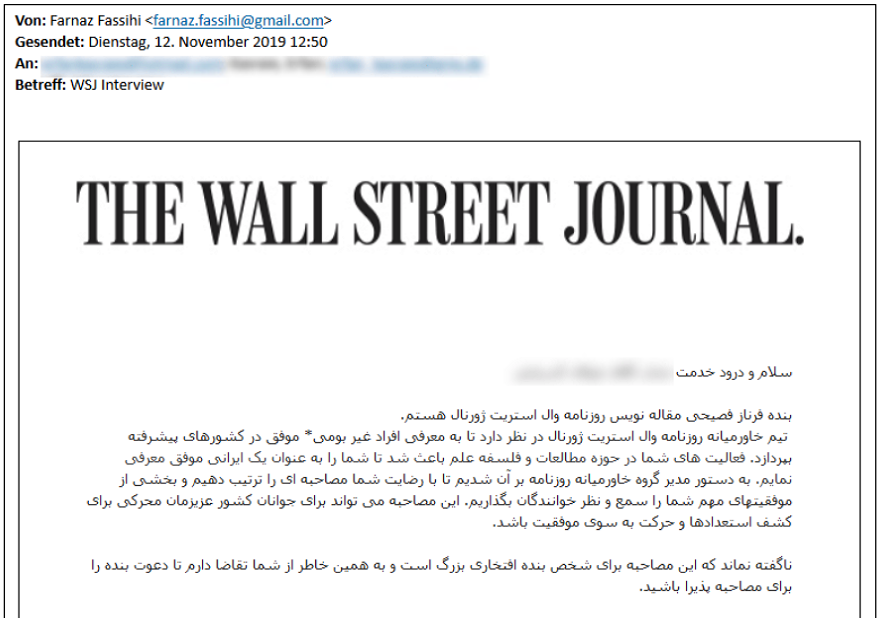
In 2020 charming kitten began a new campaign that used fake interviews to target public figures to launch phishing attacks and steal victims email-account information. This new campaign had several steps, APT35 first posed as a former Wall Street Journal journalist and gave victims an email asking for interviews in an attempt to gain trust.
The emails included links that seemed legitimate from social media, the Wall Street Journal and Dow Jones websites in short URL format, if the victim had clicked on these links charming kitten would have been able to find their IP, user agents and operating systems
Once the trust had been established, the hackers sent an exclusive link to their victims as a file containing interview questions. When the victim clicked the download button from the location of the malicious file they were sent to a fake authentication page that requested their email, password and 2 factor authentication code.
2021 – British Scholar Campaign
This form of attack was used again in 2021 when the hacking group masqueraded as British scholars to covertly target people of intelligence interest
Conclusion
For seven years the Iranian hacking group Charming Kitten has used a number of methods to target what it sees as Irans enemies and it has come a long way from its birth in 2014 with its poor examples of hacking skills. The group became famous in 2017 when it hacked HBO and the group continues to evolve its techniques and rightly holds its place as one of the top APTs currently active in the world