Poor security incriminate MuddyWater, MOIS in malicious cyber campaign
MuddyWater the APT linked to the Ministry of Intelligence and Security who got their name due to confusion in attributing a wave of attacks that took place in 2017 has been caught running a number of malicious cyber campaigns against various telecommunications, defense, local government, and oil and natural gas sectors.
Latest Exposure
Since its beginning the MuddyWater group have been known for poor security , routinely leaving details in their malware that cyber security experts are able to use to identify different types of information about them. It seems like the group has again accidentally revealed its techniques, tools, and procedures for cyber security experts to find, all due to sloppy work. In response to an anonymous tip off stating there was poor security measures employed by the group, ICNA has been able to verify that at the time of writing, several IP addresses belonging to the group had unsecured or open ports which allowed anyone with basic knowledge to access their materials.
The FBI in America have now issued an advisory warning that the group has started to use a new malware strain in its global attacks and the advisory lists various tools used by the group such as PowGoop, Small Sieve, Canopy, Mori, POWERSTATS, Survey Script as well as a newly identified PowerShell backdoor.
The advisory goes on to describe in detail how the group carries out its attacks, exposing details of known MuddyWater IP addresses as well as in depth information on how the groups malware works and how they implement it. They then go on to advise companies on how they can mitigate against these attacks.
Is MuddyWater the best Iran can get?
While other hacking groups in Iran have gained notoriety for disruptive, data-wiping attacks against middle east organizations, the group known as MuddyWater has become better known for its relentless spying efforts.
Vikram Thakur a technical director at Symantec, a division of software maker Broadcom stated that “These actors are extremely focused in what they’re doing, They’re not using zero days. They’re just looking for commonly available methods along with their custom malware to get into these environments, exfiltrate whatever they want and then move on.”
Analysis by cyber security experts suggest the group continues to evolve and adapt their techniques while still relying on publicly available malware. Despite broad scrutiny and reports on the MuddyWaters attacks the group only change their tools and techniques incrementally and like many other Iranian APT the group displays less sophistication and technological complexity compared to other state sponsored APT groups.
Although this group lacks sophistication and skill it does not seem to prevent them from pushing aggressively. This APT is proving themselves to be more like amateurs pushing their way to the goal rather than professionals with expertise that you would expect from a state actor. Their latest mistake may be one mistake too many for the Ministry of Intelligence and Security, only time will tell if their lack of skill will finally bring about an end to this notorious APT but surely this has brought about embarrassment for both the APT and MOIS.
We previously wrote about MuddyWater and other Iranian APT which can be found here.
Further Reading:
Who are MuddyWater?
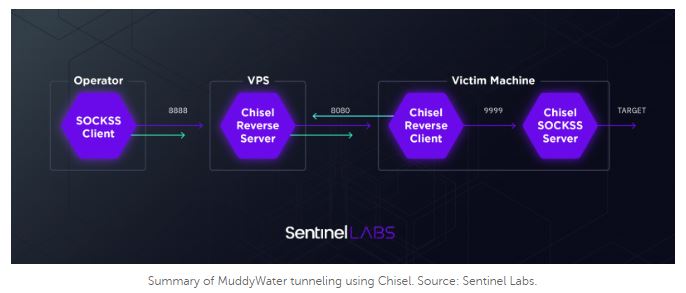
MuddyWater is a group inside the Ministry of Intelligence and Security that has been active since 2018 it is known to use a wide range of tools and techniques in its operations. The group is known by a number of names in the cyber security community such as Static Kitten, Seedworm, Earth Vetala and MERCURY and has been seen primary targeting middle eastern nations but have been seen attacking countries such as India and the USA. The groups attacks are characterized by the use of a slowly evolving PowerShell-based first stage backdoor called POWERSTATS, the group are very fond of tunneling and custom tools that often provide limited functionality and are used to drop malware enabling a wider set of activities.
History of MuddyWater attacks
2017 – First reported by Palo Alto Networks a series of malicious files were discovered affecting systems in nine countries including Saudi Arabia, Iraq, Israel, India, Georgia and the USA these files were almost identical to malware that had previously been found in Saudi Arabian government computers and had been adjusted according to the target region, often using logos or branches of local government, prompting users to bypass security controls and enable macros.
2018 – MuddyWater targeted organizations in Turkey, Pakistan and Tajikistan with a similar campaign that had targeted Saudi Arabia, The attackers used documents that mimicked government organizations such as the ministry of internal affairs or the republic of Tajikistan even using official government emblems. Researchers at cyber security company Trend Micro found text and file names in the Tajik language attempting to target individuals working for government and telecommunication companies. Each document use social engineering to trick potential victims into clicking to enable macros and activate hidden payloads. While some of the payloads were observed embedded inside documents others were also downloaded from the internet after the lure was clicked.

2018 – The group was caught targeting victims in Lebanon and Oman leveraging compromised domains to deliver macro-enabled documents that were designed to look like resume applications from the ministry of justice in Lebanon or Saudi Arabia. Like the other attacks once enabled these macros activated payloads that further infected the victims systems
2019 – A large number of spear-phishing documents were discovered that appeared to target government, military, education and telecommunication institutions in Jordan, Turkey, Azerbaijan and Pakistan. Like before these documents relied on social engineering to persuade users to enable macros. The group relied on a range of compromised hosts to deliver their attacks however cyber security experts at tech company Securelist were able to to observe a number of OPSEC mistakes made by the attacker, these mistakes would continue to plague the group until the present day.
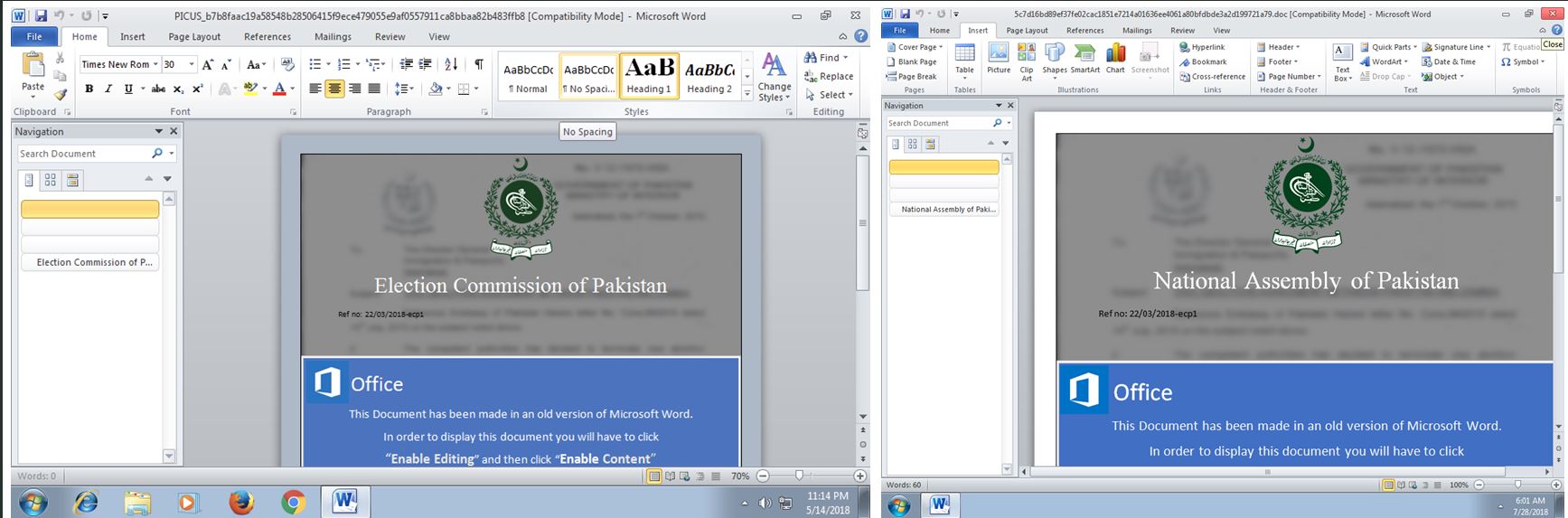
2019 – The group targeted Kurdish groups and various organizations in Turkey affiliated with the army and defense sector. The initial infection vector was via emails attached with malicious word documents. Below is a screen capture of a document sent tot he Kurdish party. The blurred image is an example of a fake official document of the Kurdistan Regional Government. The target is prompted to enable editing or enable content to properly view the documents content, however this executes an embedded malicious macro command.
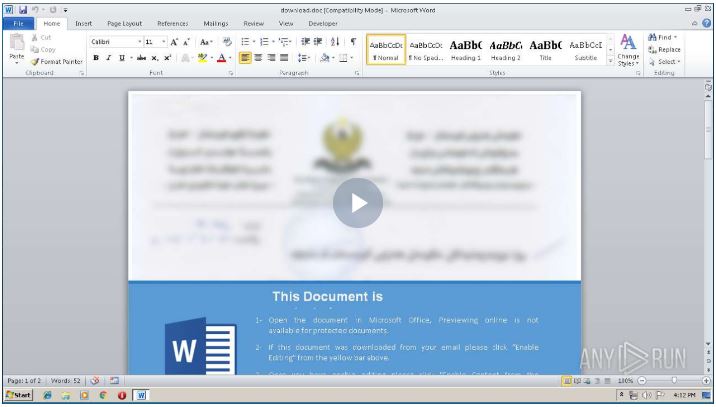
2020 – MuddyWater was detected attempting to hack dozens of government agencies and telecommunications companies in Iraq, Kuwait, Turkey and the United Arab Emirates, The attacks appear to be trying to smuggle key data from the organizations they managed to breach. These attacks were the first time the group started to use a new tool called PowGoop which once installed on a victims computer allowed the installation of other programs capable of siphoning data off of networks. During this time the group began to shift away from solely scripting-based tooling such as Powershell and moved from .NET and custom C++ payloads
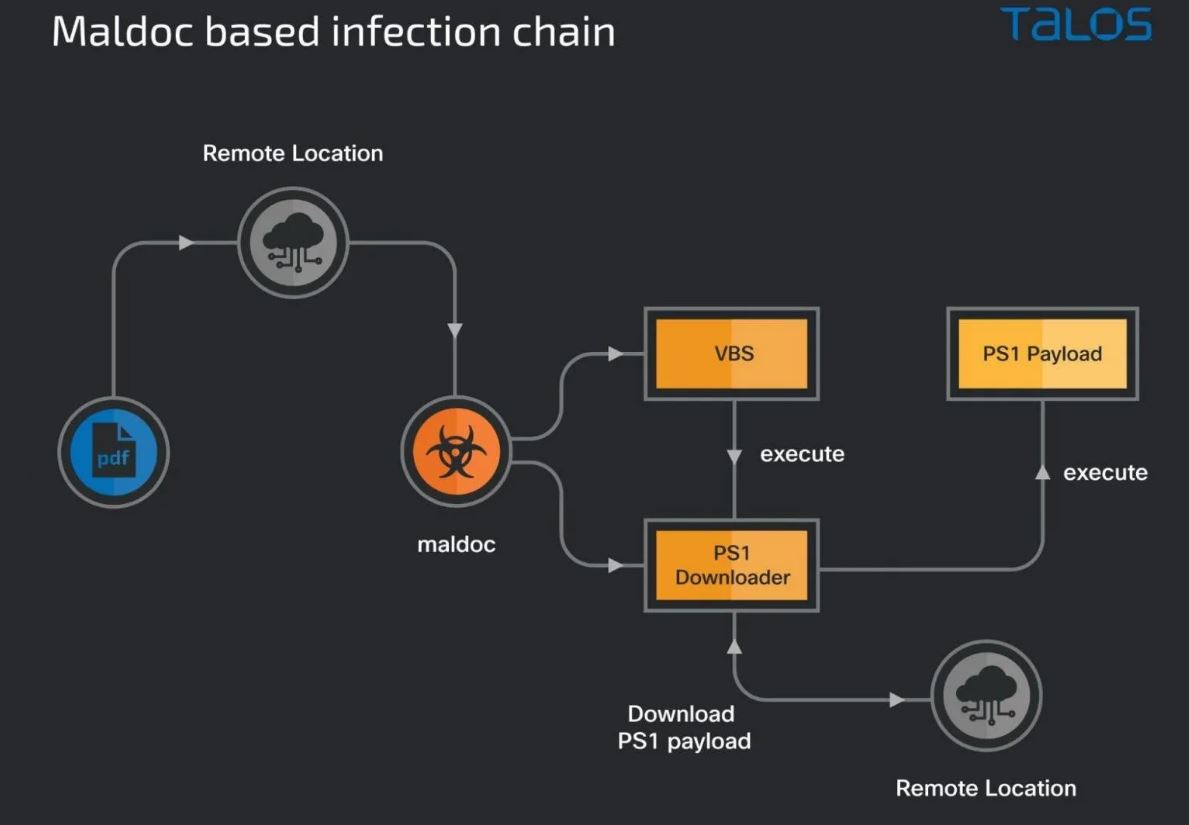
2021 – MuddyWater was officially linked to the Ministry of Intelligence and Security by US Cyber Command after an operation by the group was discovered targeting Turkish telecommunication and government IT systems. Much like all the previous attacks the group used malicious PDFs and Microsoft office documents as the initial infection vector, the bait documents masqueraded as legitimate documents from the Turkish Health and Interior Ministries, Upon opening the documents a malicious PowerShell based down loader gave the group an initial foothold into the targets network. Once inside the network a second PowerShell script in the metadata of the weaponized document downloads a third malicious script that ultimately runs on the infected endpoint. This attack was the first time the group was observed using canary tokens in the macro code to track successful infections, evade sandbox-based detection systems and detected if the payload servers were being blocked.
In total since 2017 it is believed that the group has compromised 0ver 130 victims in 20 organizations all over the world, from Russia to Saudi Arabia to North America





