35/000 Characters Tweet Shocks German Hackers!
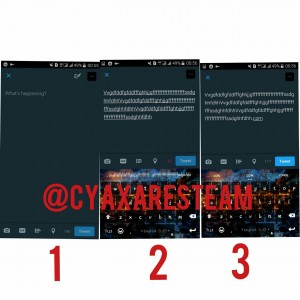
Thinking that a person could send a tweet with more than 280 characters is more or less like a dream. One can say that, this is for the first time that a person could go round this limitation. In the past, Twitter allowed each person to send a tweet with maximum 140 characters, recently this limitation has been changed to 280 characters. Finally the German hackers used their creativity to send a 35/000 characters tweet, which shocked the users of this social network and also the managers of Twitter.
These hackers after sending this tweet said their goal was to just show the weakness in Twitter and reminded that this has been only a first step to showing this kind of vulnerabilities.
But how did they go round this limitation?
According to the research that H.BBF3.4 did, he easily found the method that was used by these creative hackers. In sending the tweet, you first write whatever you want in English but without putting space between the words. It doesn’t matter how many characters you write. Just at the end you write .com or any other domain so that Twitter is fooled.
For example: SvFnafnafhdsgqifackacnackakcpcakcjanckackacnacjqkckaclaclacnacanckakvoackcjacixpapxaoxkack.com
Sending this kind of tweets cause that the Twitter server is disrupted and this social network is out of service for one hour. Of course after sending this tweet Twitter quickly took action to delete it and to close the tweeting person’s account but after a few hours this person’s account returned to normal state.
After they sent this tweet the hackers apologised to Twitter and the managers of Twitter also announced that the problems about sending this kind of tweet has been solved.
Don’t forget that security is never 100%, and one day even the big and famous companies will be penetrated, this penetration can be the kind of publishing users information or, like the 35/000 characters tweet it can publish information about a vulnerability.
