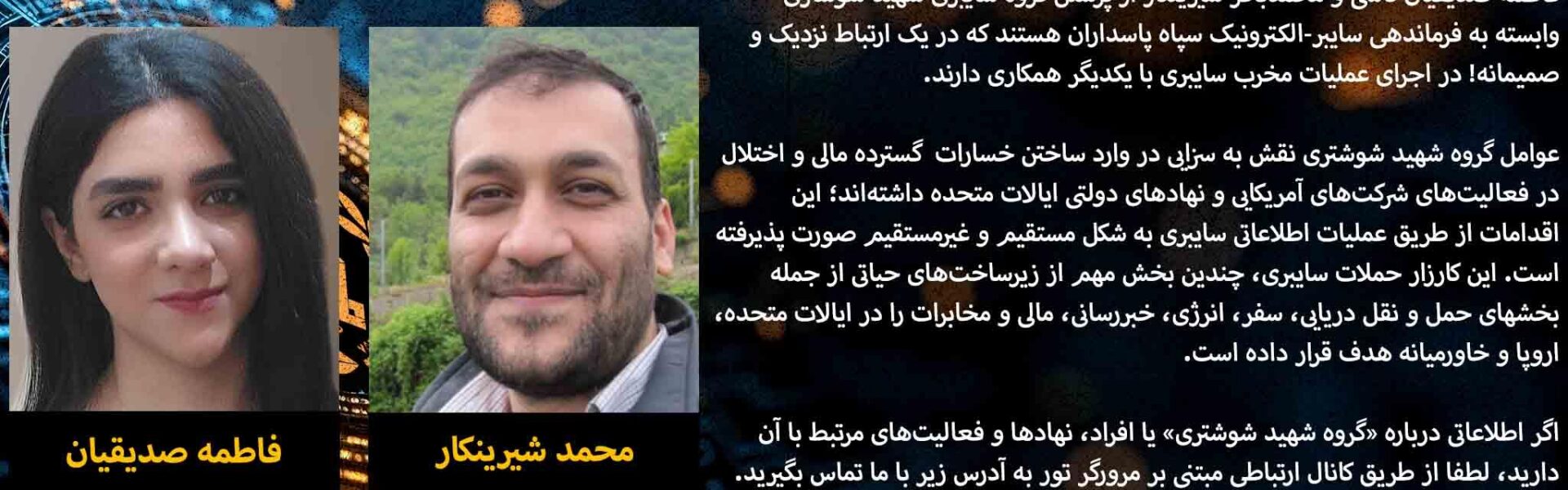
The US State Department’s “Rewards for Justice” program has announced a reward of up to $10 million for information leading to the identification or location of Mohammad Baqer Shirinkar, and long-time employee Fatemeh Sedighian Kashi.
The US Government is looking for information regarding members of Emennet Pasargad, an Iranian state-sponsored threat actor group that has been active in cyber operations targeting entities perceived as hostile to the Iranian regime.
The threat group has also been known as Aria Sepah Sazan (ASA), Aria Sepehr Ayandehsazan, Marnanbridge, Cotton Sandstorm, Eeleyanet Gosta, Haywire Kitten and Net Peygard Samavat Company. The US now calls the group Shahid Shushtari and states that the group is operating under Iran’s Islamic Revolutionary Guard Corps Cyber-Electronic Command (IGRC-CEC).
According to the US, these hackers are operating out of Tehran and are conducting cyber attacks against critical infrastructure in the US, Europe and the Middle East. Shahid Shushtari has been blamed for the 2024 Paris Summer Olympics attack and was previously sanctioned for operations targeting the 2020 presidential election. The FBI has previously reported that Emennet Pasargad conducts hack and leak operations against organisations primarily in Israel. Following the 2023 Hamas attack on Israel, the group attempted to contact family members of Israeli hostages through fishing in an effort to cause additional psychological stress. They also attempted to identify information concerning Israeli fighter pilots and UAV operators by searching for information across multiple platforms. The FBI also reported in 2024 that Emennet Pasargad were using the Iranian company name Aria Sepehr Ayandehsazan as a nominal cover, including for human resources and financial related purposes.
The US has urged anyone with information on either employees or the group to contact Rewards for Justice via the Tor-based tip reporting channel.