Sepehr Energy Jahan Company Hacked
Sepehr Energy Jahan Company has been hacked. Today, Anonymous announced that they had successfully attacked and infiltrated the company’s network and extracted approximately 6 Gb of data. It is worth noting that this hacker group was a member of the…
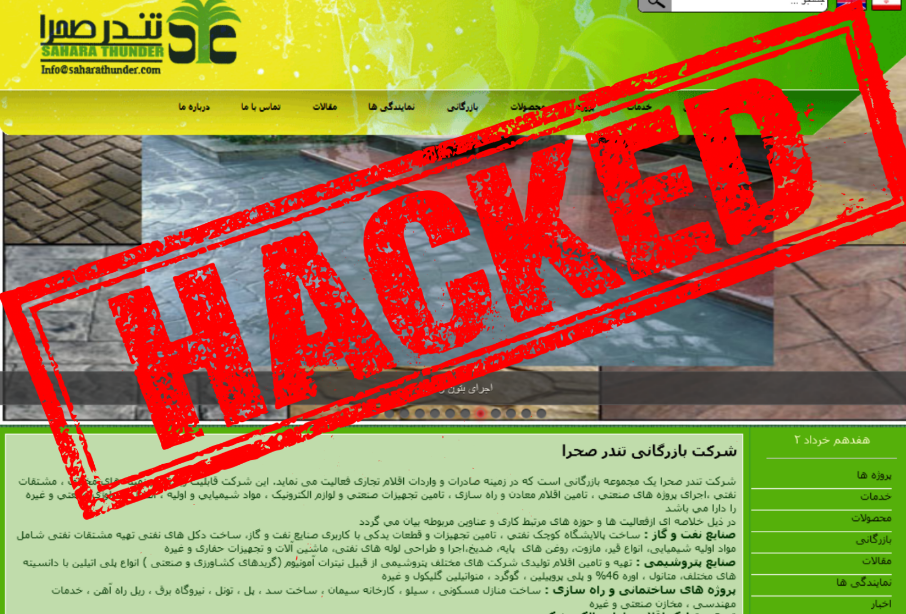
IRGC Front Company Sahara Thunder Hacked by PRANA Network
On 4 February 2024, PRANA Network announced that they had successfully hacked the email servers of an IRGC front company called Sahara Thunder who are facilitating the illegal sale of weapons from Iran to Russia. This data which…
Privacy vs Anonymity
Guest written by Laurtis Vestergaard In the first post of our series on setting up VPNs we covered the basics of how to set up a VPN what equipment is needed. If you missed it you can read it here….
How to set up a VPN
Guest written by: Laurtis Vestergaard In these next series of blogs, we will walk you through the various methods on how you can set-up a commercial VPN or create your own for secure online browsing. Previously we have looked at…
An updated history of Anonymous hacking group
Maybe you remember that approximately a year ago we published a report about the history and activities of Anonymous hacking group but what exactly has this group been doing since that time. Of course this group has been continuing their…
FSB, Russian industry leaders and government officials travel to Iran – Safiran data
After publishing our initial article about the group Hooshyarane Vatan’s hack of Safiran, we have had a bit of time to look at the data some more. We wanted to know who the Russian visitors to Iran were so started…
Hooshyarane Vatan hack Safiran
The cyber group known as Hooshyarane Vatan has once again exposed an Iranian company working with the IRGC. Read about their previous attack here and here. This time it is Safiran airport services who have been facilitating weapons and UAV…
Anonymous continues attacks as part of Op Iran
Dear reader since we published our report on the history of Anonymous the collective has continued attacks as part of OpIran. They have been able to hack many sites. They also recently have hacked IranCell and obtained the data of…
Hacked by Anonymous: Part Two of 4chan to Iran
Dear readers in our last article we describe how famous hacking group Anonymous was first formed from the website 4chan and went on to become famous for Hacktivist attacks across the world. In this next article we talk about Anonymous…
An Anonymous History: From 4chan to Iran
Dear readers in August the hacking group Anonymous first turned its eye on Iran, a group calling themselves The Sword of Anon released image of Saif al-Adl a high level member of al-Qaeda alongside number other member located in Tehran,…