Cyber campaign “Red Kitten” targets human rights activists and NGOs
“Red Kitten” is an advanced persistent threat group affiliated with the Islamic Revolutionary Guard Corps (IRGC), which started its activities in January 2026, during the country-wide protests. It appears that the group has conducted a campaign targeting NGOs and human…
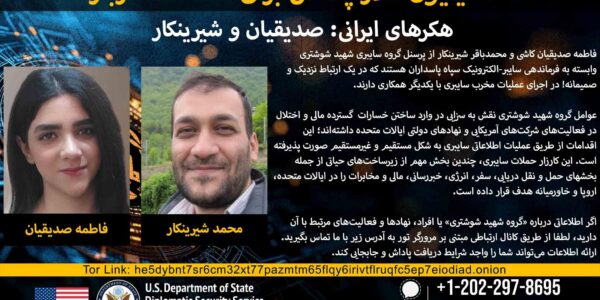
Up to $10 million reward for information on Iranian hacking group
The US State Department’s “Rewards for Justice” program has announced a reward of up to $10 million for information leading to the identification or location of Mohammad Baqer Shirinkar, and long-time employee Fatemeh Sedighian Kashi. The US Government is looking…
What actually is a strong password?
Guest written by: Laurits Vestergaard What actually is a strong password? Increasingly our lives are online, thought innumerable online accounts all of which require a password. There are constant stories of data breaches and hacks where hackers have taken advantage…
Is Physical security missing from your cybersecurity policy?
Physical security is an often forgotten or overlooked part of a corporate cybersecurity policy. To be effective a cybersecurity policy must be able to counter a cyberattack at any stage of what cyber experts call a cyber-kill chain. …
Poor security incriminate MuddyWater, MOIS in malicious cyber campaign
MuddyWater the APT linked to the Ministry of Intelligence and Security who got their name due to confusion in attributing a wave of attacks that took place in 2017 has been caught running a number of malicious cyber campaigns against…
Famous Malware: Part four of the Hacker Series
Dear readers for part four of our hacker series will talk about some of world’s most famous malware. The tools are used by APTs to attack their victim and cause major damage Emotet 2018 Our first famous malware…
The increasing problem of hacking in Iran
Dear reader today I wish to talk to you about the increasing problem of hacking in Iran The increasing problem of hacking in Iran began in December 2009 there are many reasons why someone decide to begin hacking, for some…
BLACK SHADOW hack of Israeli company not for political revenge
A hacker group by the name of Black Shadow leaked images of ID cards, drivers licenses and other personal information on a Telegram channel after carrying out what the group says a massive cyber attack. On 1 December a Twitter…
The Internet of Things and its future in Iran
Technological readiness and investment The Internet of Things (IoT) is a term that refers to a network of physical objects that are able to connect with each other and exchange data over the internet with only little human intervention. In…
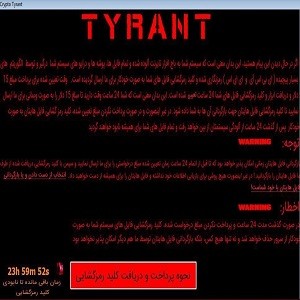
Iranian TYRANT Ransomware
A new type of ransomware have been discovered on October 16 2017 which appears to be Iranian. The Tyrant Ransomware is a data encryption Trojan that is classified as a mid-tier crypto-threat. The threat appears to be used in attacks on…