On November 10th a government website (e-monitor.ito.gov.ir) belonging to the Information Technology Organization of Iran (ITO) was the target of a hack. ITO is responsible for administration and regulation of matters connected with IT sector in Iran and for taking forward projects for improving connection of people to electronic government.

News of the hack was reported on IRGC Telegram groups such as the one in the image below and on social media, and as an article by different Iranian news services.
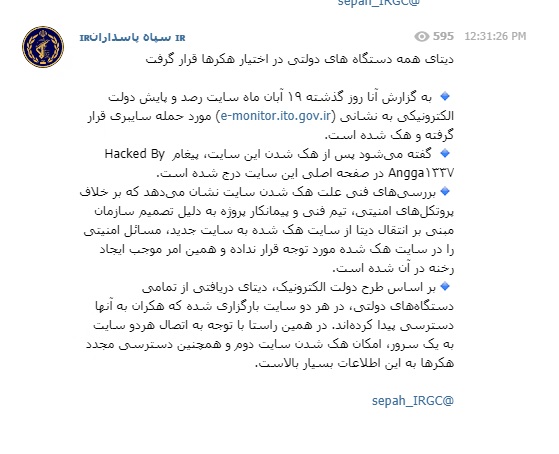
The group responsible for the hack
The hacking group called ANGGA1337 have taken responsibility for the attack. This group was reported to made the website inaccessible and posted the message “Hacked by ANGGA1337”.
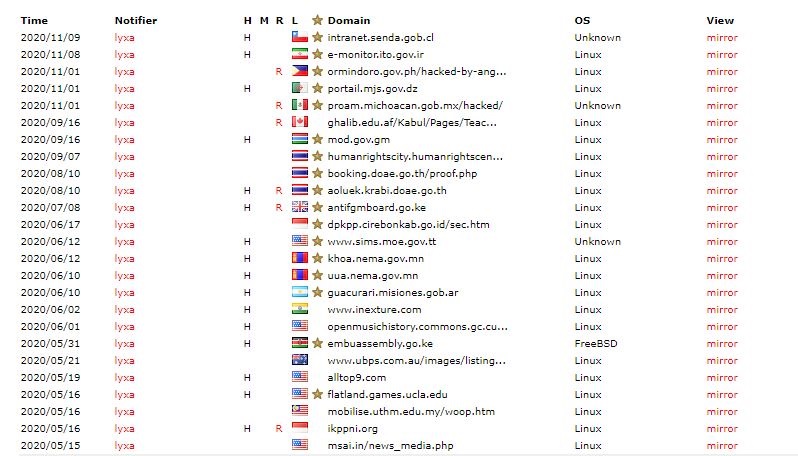
The record from Zone-H indicates that the group has been busy in 2020, hacking a large number of websites, but actually Iran is not a common target of the hacking group. The websites hacked originate from many different countries and include a small number of .gov and .edu domains. The different type of websites attacked and the different locations indicate that it is more likely that they are hacking in order to make money, for example from ransom of the details stolen, than for any political or moral motivations.
The group have a profile on the website raidforums.com which is a website used by hacker to upload hacked data to sell or share. It appears the group’s raidforums account was only created a few days before carrying out the attack on the ITO website. The Twitter page of Angga (@firew4ll)that was created in 2009 has not been used to post Tweets since 2015. It uses Indonesian language which is in agreement with suggestions that the group are based in Indonesia. IT also gives the website (anggga.or.id) that has existed for almost 10 years indicating that this is not a new group.

The group have a Youtube channel with 85 subscribers which was created in December 2019. This channel is used by Angga to share videos on hacking techniques and tutorials such as how to upload a shell to a webserver (a shell is a computer program that gives a command line interface that human or another program can use to control the operating system). The logo appears to show the group name in Japanese and in English language.
ITO and social media response to hack
Twitter user @mjnanakar said the data of 23 priority e-government projects was stolen. There is no mention of the hack on the ITO Twitter account (@ITOofIRan) but the ITO has written about the attack on their website (ito.gov.ir).
It is necessary to say that the ITO confirmed the attack but they say that the data that the hackers stole was already available to the public and that confidential and sensitive data held on the website was protected from the hack. The Deputy Minister of Communications and head of the ITO said that the hackers only defaced the system at a superficial level.
The detail of the attack indicates to us however that this might not be true and the statements by the ITO also have been questioned on Twitter by users tagging the ITO in their tweets. These Tweets also show anger at those responsible in the government for not protecting the data on their websites. There are some accusations that the site (e-monitor.ito.gov.ir) was vulnerabl3e as a result of the way that it been set up, with a second site (remonitor.ito.gov.ir) on the same server even though the government knew about the vulnerability of the first site. Pay attention to the fact that according to one journalist (@aboali313_1), the posting of the data of full status report of e-government projects to the first site was illegally done without authorization of IT Executive Council, which the head of this Executive Council is Hassan Rouhani, the president of Iran.
Ignoring the warning signs
There is concern also that this hack happened despite many recent attacks on other government websites. For example Zone-H records show evidence that since January a large number of ict.gov.ir domains were hacked by ‘OP999’ (we are researching these hacks for another article). It is clear that ITO did not learn from these lessons and make the necessary changes to protect their site. There is also some criticism that Iran’s information security and intelligence agencies are not doing enough to protect against internal and external attacks.





